Playbooks, Workflows, & Local Instance Examples
IACD provides a mechanism where business- and operations-driven objectives, processes, and controls—including those captured via a Cybersecurity Framework profile—can be translated and applied as automated response actions. Via IACD playbooks, conditions, indicators, and controls that drive the need for cybersecurity responses are captured for orchestration services to monitor and execute. Learn More
Detail at the Three Levels of Orchestration Abstraction
Playbooks and Workflows
The following example playbooks and workflows are categorized using the NIST Cybersecurity Framework's Five Functions: Identify, Protect, Detect, Respond and Recover. These five functions represent the five primary pillars for a successful and holistic cybersecurity program. More information on these functions can be found here.
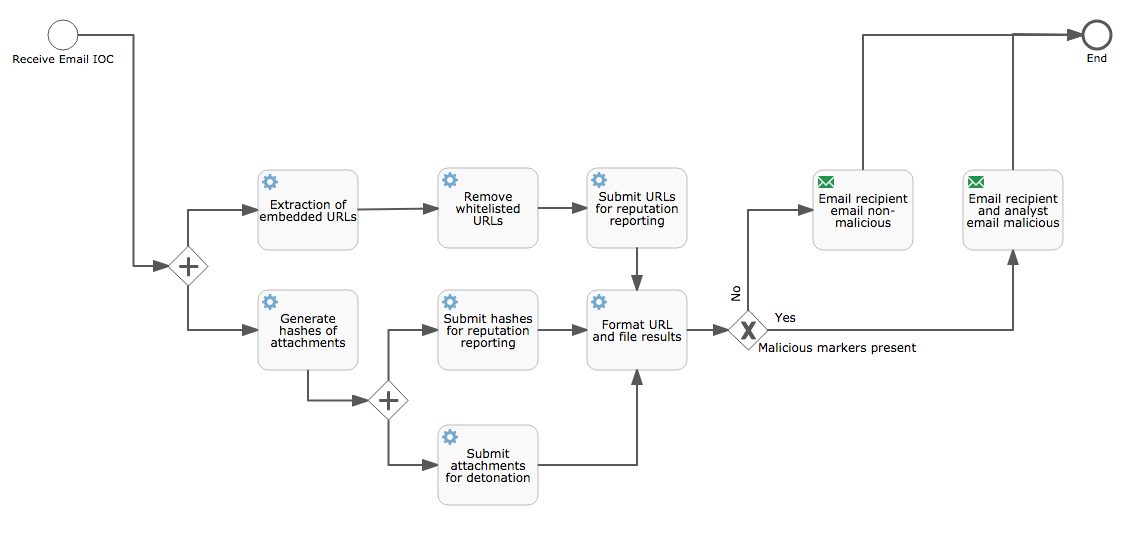
Workflows have been built using an open source Business Process Model Notation (BPMN v2.0) tool and the associated XML (.bpmn) files are available for download. To view the legend for different types of events, tasks, and gateways in a workflow, check out the Operational Best Practices IACD Reference Workflow Template.
Note: While there may be some overlapping across functions, these example playbooks and workflows are organized corresponding to the most prevalent function.
Identify
The Identify Function assists in developing an organizational understanding to managing cybersecurity risk to systems, people, assets, data, and capabilities.
Playbooks:
Mitigate High Risk Device: Process for identifying a high risk device on a network and restoring the device to an authorized state.
Related Workflows:
USB Media Restrictions: Process for examining and alerting on USB media use.
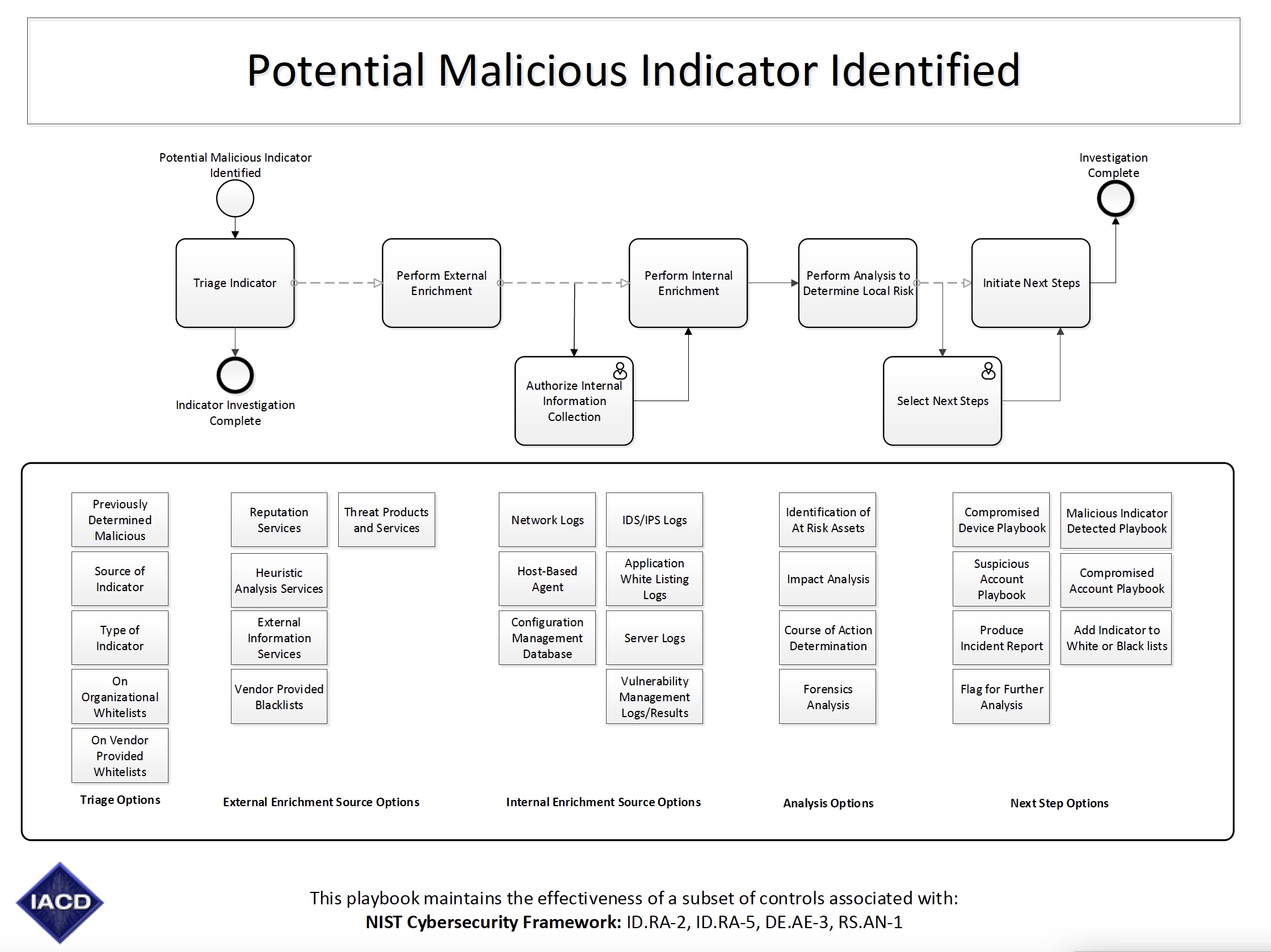
Potential Malicious Indicator Identified: Process for investigating and responding to a potential malicious indicator identified on the network.
Related Workflows:
Firewall Alert - Generic: Process for dealing with and enriching firewall alerts. Can lead to Unknown URLs or Threats and Traffic workflows.
Firewall Alert - Unknown URLs: Process for enriching unknown URL firewall alerts. Triggered by Firewall Alert - Generic workflow.
Firewall Alert - Threats and Traffic: Process for enriching threat and traffic firewall alerts. Triggered by Firewall Alert - Generic workflow.
Notification of New Potentially Malicious File on Network: Process for enriching, storing enriched information, and notifying analysts about new files on the network.
Protect
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services.
Playbooks:
Disable Account for Outgoing Employee: Process for disabling account access for an employee who is scheduled or has left an organization.
Detect
The Detect Function defines the appropriate activities to identify the occurrence of a cybersecurity event.
Playbooks:
Advanced Autoimmunity Analysis: Process for performing an autoimmunity analysis as a result of a periodic analysis of a network.
Workflows:
Malware Detection Response: Process for enriching malware detection alerts.
Rogue Alert: Process for enriching and blocklisting rogue alerts.
Suspicious Email: Process for enriching and examining suspicious emails.
Virus Alert: Process for enriching and alerting on virus alert.
Respond
The Respond Function includes appropriate activities to take action regarding a detected cybersecurity incident.
Playbooks:
Autoimmunity Analysis of Submitted CTI: Process for performing an Autoimmunity analysis on submitted cyber threat information.
CTI Flagged Following Autoimmunity Analysis: Process CTI that has been flagged by a CTI autoimmunity analysis by generating an enriched Alert for the flagged CTI which results in updated profiles.
CTI Passed Autoimmunity Analysis: Process CTI that has passed a CTI autoimmunity analysis by generating enriched CTI, which results in updated profiles.
Determine Remediation Action: Process for identifying a response action as a result of a loss of internal service
Malicious Indicator Detected on Network: Process for investigating and responding to a malicious indicator identified on the network.
Related Workflows:
Threat Feed to Blocklist: Process for updating blocklists.
Scan for and Mitigate Malware on Servers: Process for identifying malware on a server and restoring the server to the authorized state.
Recover
The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
Mitigate Compromised Device: Process of identifying a compromised device on a network and restoring the device to an authorized state.
Mitigate Compromised Local Administrator Credential: Process for restoring a compromised local admin credential to an authorized state.
Rebuild Server After Loss of Heartbeat is detected and investigated: A critical service was identified as not having a heartbeat. Investigate the cause and rebuild the critical service.
Rebuild Server Playbook: Process for rebuilding a server that was removed from the network.
ShareaBle Workflows from APL SLTT Pilot
The Johns Hopkins University Applied Physics Laboratory has developed additional shareable workflows for the scoring, sharing, and response to cyber Indicators of Compromise (IOCs) for the State, Local, Territorial, and Tribal (SLTT) community. The workflows and report are available here.