Best Practices and Guides for Security Automation and Cyber Threat Intelligence Sharing
A collection of resources to help you and your organization protect your networks against cyber attack.
Cybersecurity Automation and Threat Intelligence Sharing Best Practices Whitepaper Series
This series of papers are developed to provide you high level understanding and insight for your efforts to utilize Cyber Threat Intelligence (CTI) sharing and Security Orchestration Automation and Response (SOAR) for your security operations
Assessing the potential value of Cyber Threat Intelligence (CTI) Feeds
Questions to ask yourself as you choose the right CTI feed for your needs
Deploying Indicators of Compromise (IOCs) for network defense
Better understand the operational value of IOCs
Understanding Service Models for Cyber Threat Intelligence
A deeper look at Intelligence, Enrichment, and Brokering as a Service
Preserving CTI Content
Understand how certain infrastructure choices impact the content of your CTI.
Assessing Automation Potential of Products and Services
Questions to ask yourself as you select your tools and services for SOAR integration
Increasing Automation Potential of Processes
Questions to ask yourself as you transform your manual security processes to automated ones
Strategy for Efficient Process Automation
Concepts to help you develop a strategy for SOAR implementation to handle both speed and scale.
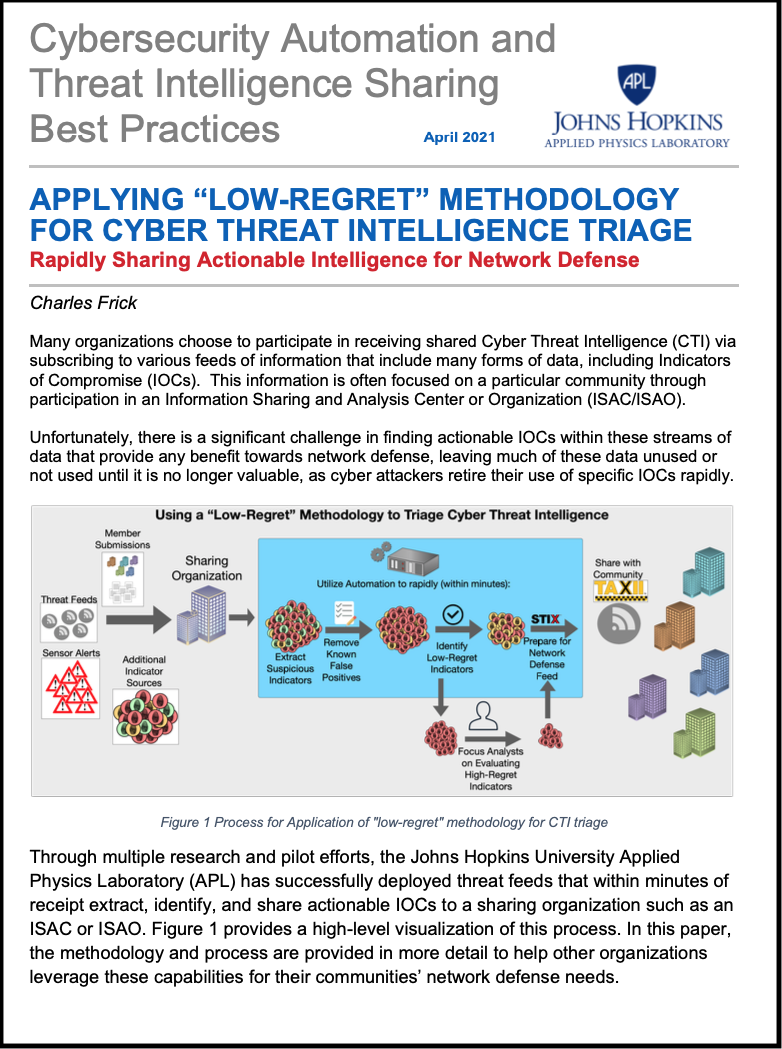
“Low-Regret” Methodology for CTI Triage
Process on how to rapidly share actionable CTI for network defense.
“Low-Regret” Methodology for CTI Response
Process on how to rapidly process, decide, and respond to incoming CTI with a focus on network defense.
Orchestration of Information Technology Automation Frameworks
Insights to better understand the difference between Security Orchestration and IT Automation and how to use them together
Information-Centric Automation and Orchestration
An overall guide to how to focus your capabilities to enable an architecture that brokers information with a focus on your network defense.